GDPR Export Description
General Infoarmation
The GDPR export contains all collected information/results of the performed GDPR scan(same information as in the Nimbusec compliance monitor).
Information is split in 4 main categories
All collected information/results were generated before any kind of user interaction with the website was performed No cookies etc. were accepted when visited the website[except the cookie banner feature was enabled (optional)].
The Excel Document itself contains 5 different data sheets
The "Assets" sheet contains all websites that were scanned for compliance.
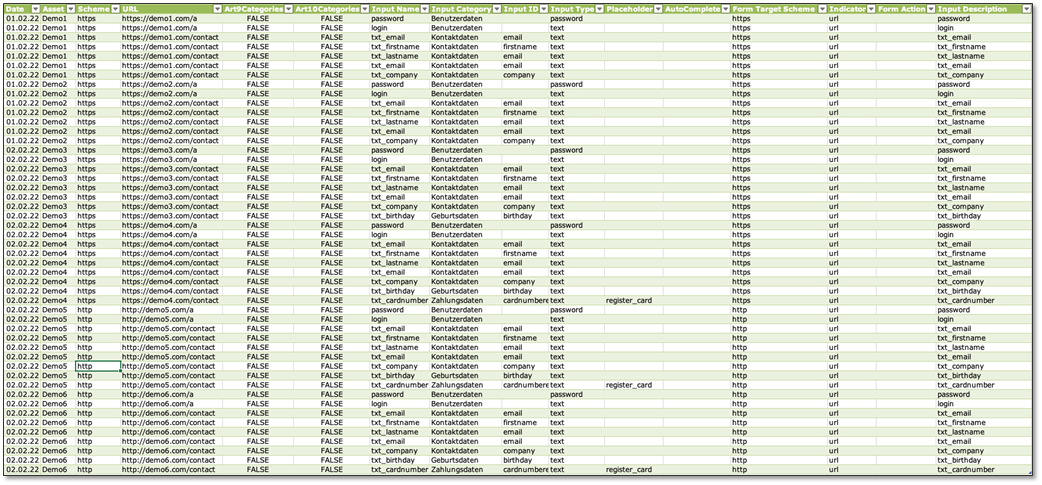
Inputs
This section focuses on input forms that handle sensitive data. Our scanner collects all form fields that are present on your web-applications.
Simply put: A complete inventory of all input forms on all domains in scope.
Table fields explained
- Date
Shows the date when this information was discovered - Asset
Indicates the start point that was scanned - Schema
Which HTTP schema was used for the scan (HTTP/HTTPS) - URL
Shows the exact URL of the detected input form - Art 9/10 Category
True shows a violation against this specific case - Input Name
Name of the detected input field (parsed from source code) - Input Category
Based on the detected input name and input type, an input category is defined Contact data, job, gender, user data, … - Input ID
Represents the unique ID of the input field (parsed from source code) - Input Type
Shows the type of the detected input field e.g. text, radio button, select, … - Placeholder
Shows, if present, the prepared default text - Form Target Schema
Shows the used schema that was used to transmit the provided data
https -> data encrypted
potentially http -> transmission schema unsure, please check manually (with e.g. Wireshark
http -> data unencrypted - Form Action
Provides the defined action for the specific form (from source code)
Next steps based on best practices (work package)
- Remove / Update unencrypted forms https
- Individual website review
- Check if forms are still necessary
- Check if placed input data is needed in the placed context
- Check if provided data is processed / sent outside your organization (third party)
- Check if all provided form data is documented in the privacy policy including the reason why this data is needed
Further Reading
Unencrypted data forms
https://eur-lex.europa.eu/legal-content/DE/TXT/HTML/?uri=CELEX:32016R0679&from=EN#d1e3385-1-1
https://www.mein-datenschutzbeauftragter.de/blog/datenschutz-auf-websites-warum-die-verschluesselung-von-kontaktformularen-etc-wichtig-ist/
https://gdpr-info.eu/issues/encryption/
https://www.ra-plutte.de/gastbeitrag-warum-sie-ihre-website-auf-https-umstellen-sollten/
Personal Identifiable Information (PII)
https://eur-lex.europa.eu/legal-content/DE/TXT/HTML/?uri=CELEX:32016R0679&from=EN#d1e2066-1-1
Third Parties
https://www.usp.gv.at/it-geistiges-eigentum/datenschutz/einwilligung.html
https://dsgvo-gesetz.de/themen/auftragsverarbeitung/
https://www.lda.bayern.de/media/veroeffentlichungen/FAQ_Abgrenzung_Auftragsverarbeitung.pdf
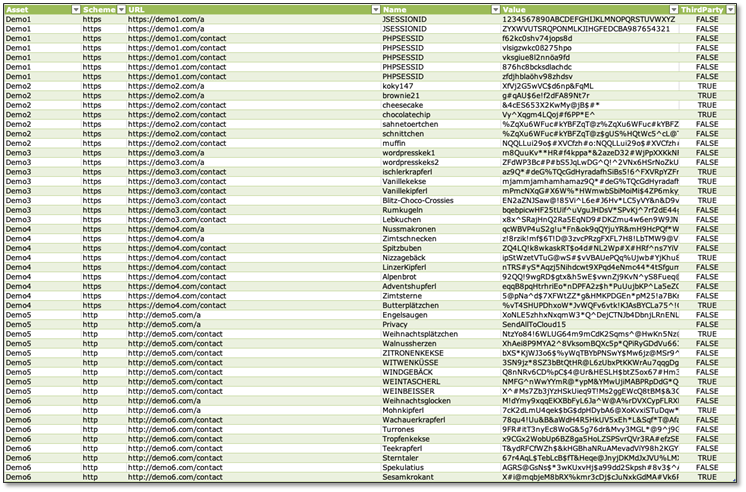
Cookies
This section focus on detected cookies of the scanned websites. Since our scanner does not interact with the website, all detected cookies were set before user consent.
-> A full documentation of all set cookies (before user consent) of all scanned web-applications.
Table fields explained
- Date
Shows the date when this information was discovered - Asset
Indicates the start point that was scanned - Schema
Which HTTP schema was used for the scan (HTTP/HTTPS) - URL
Shows the exact URL of the detected cookieIn case of a manual review, please check this URL - Name
Includes the name of the detected cookie - Value
Shows the set value of the detected cookie - Domain
Shows the domain that sets the detected cookie - ThirdParty
Has a direct relation to the Domain column, if the Asset and the Domain is not equal (based on domain level) a third party sets this cookie
Next steps based on best practices (work package)
- Check all detected cookies and classify them as “technically necessary” or not (depends on the application)
- Implement/Update a cookie banner to ensure that all ”non technically necessary” cookies were set after user consent
- Create/Update privacy policy / cookie policy and list all used cookies
Further Reading
https://curia.europa.eu/juris/document/document.jsf;jsessionid=F2A804042CAC4FE3D70A00596C6A76D0?text=&docid=218462&pageIndex=0&doclang=DE&mode=req&dir=&occ=first&part=1&cid=1686588
https://www.wbs-law.de/it-und-internet-recht/datenschutzrecht/eugh-cookies-aktive-einwilligung-c-673-17-45473/
https://www.wko.at/branchen/information-consulting/werbung-marktkommunikation/eugh-entscheidung-zu-cookies-und-einwilligung.html
https://www.datenschutz.org/cookies/#die-regelungen-fuer-cookies-innerhalb-der-eu
https://www.lda.bayern.de/media/pm/pm2021_06.pdf
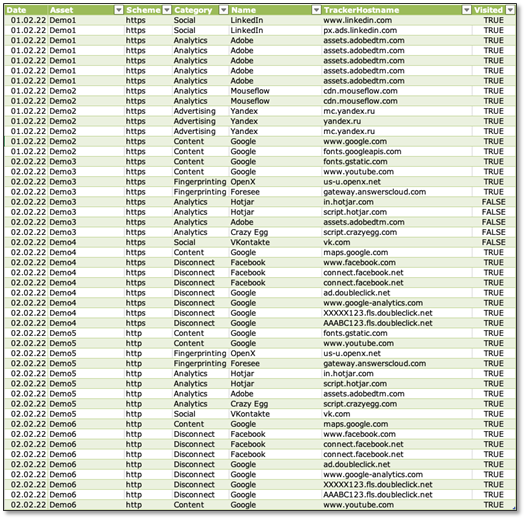
Tracker
This section focuses on internal/external used tracking software. Our scanner analyses the whole network traffic that was triggered by initially visiting the web-application. As a result, all detected requests were triggered before user consent.
-> A complete list of all used tracking technologies of each domain in scope
Table fields explained
- Date
Shows the date when this information was discovered - Asset
Indicates the start point that was scanned - Schema
Which HTTP schema was used for the scan (HTTP/HTTPS) - Category
All detected tracker will be assigned to a specific category e.g. FingerPrinting, Social Media, … - Date
Shows the date when this information was discovered - Asset
Indicates the start point that was scanned - Schema
Which HTTP schema was used for the scan (HTTP/HTTPS) - Category
All detected tracker will be assigned to a specific category e.g. FingerPrinting, Social Media, …
Next steps based on best practices (work package)
- Disable/Remove all events (that process personal user data) that were triggered by initially visiting the website (before user consent)
- Implement (if not present) a user consent banner (e.g. cookie banner)
- Create/Update privacy policy (https://gdpr.eu/privacy-notice/)
Further Reading
https://dsgvo-gesetz.de/themen/auftragsverarbeitung/
https://gdpr.eu/privacy-notice/
Content
This section focus on company specific compliance parts that were individually defined with the project team.
->A full documentation of which domain violates the defined rules
Table fields explained
- Date
Shows the date when this information was discovered - Asset
Indicates the start point that was scanned - Schema
Which HTTP schema was used for the scan (HTTP/HTTPS) - URL
Shows the exact URL of the checked ressource - OK
This flag shows if the rule (in the Rule column) is was violated or not
true = no violation detected
false = violation detected - Rule
Shows the rule that was checked for the given asset
Next steps based on best practices (work package)
- Analyze individual rule violations of each website(Why was this part not detected?)
- Apply changes to the web-application to meet the company rules